HIPAA law applies to doctors’ offices, hospitals, health insurers, and other healthcare companies, including healthcare SaaS, as well as cloud service providers, that process protected health information (PHI) on their behalf. HIPAA violation can cost a health organization millions of dollars. To be compliant, healthcare businesses must keep PHI safe (billing statements, claims requests, health status, treatment, and prescription information, test and procedure results, and visit notes) while storing or manipulating it (transfer, receive, handle, or share). In this article we focus on the data-storing aspect, around considering HIPAA-compliant databases, specifically cloud ones.
What is HIPAA-compliant Database?
A database is an organized collection of structured information controlled by a database management system. To be HIPAA-compliant, the database must follow administrative, physical, and technical safeguards of the HIPAA Security Rule. Often it means limiting access to PHI, as well as safely processing, transmitting, receiving, and encrypting data, plus having a proactively breach mitigation strategy.
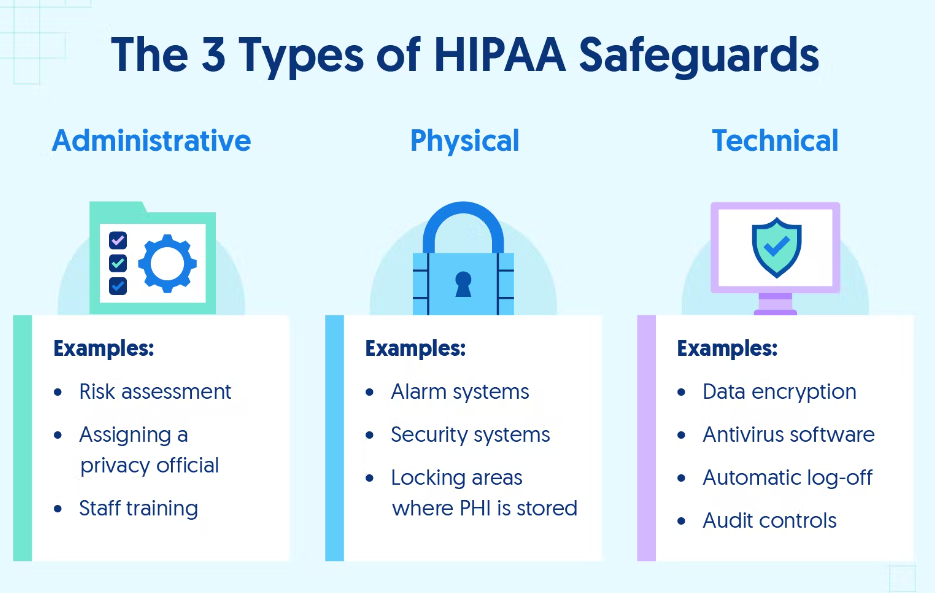
Administrative, physical, and technical safeguards of the HIPAA Security Rule
HIPAA Rules for Database Security
If your database contains even a part of PHI, it is covered by the HIPAA Act of 1996 and can attract the attention of auditors. PHI is the information containing any identifiers that link an individual to their health status, the healthcare services they have received, or their payment for healthcare services. The HIPAA Security Rule (the part of HIPAA Act) specifically focuses on protecting electronic PHI. Technical safeguards (the part of HIPAA Security Rule) contain requirements for creating a HIPAA-compliant database.
Centers for Medicare & Medicaid Services (CMS) covers HIPAA Technical Safeguards for database security in their guidance.
The first question that can arise is whether you should use any specific database management system to address the requirements?
The answer is absolutely no. The Security Rule is based on the concept of technology neutrality. Therefore, no specific requirements for types of technology are identified. Businesses can determine themselves which technologies are reasonable and appropriate to use. There are many technical security tools, products, and solutions that a company may select. However, the guidance warns that despite the fact that some solutions may be costly, it can’t be the cause of not implementing security measures.

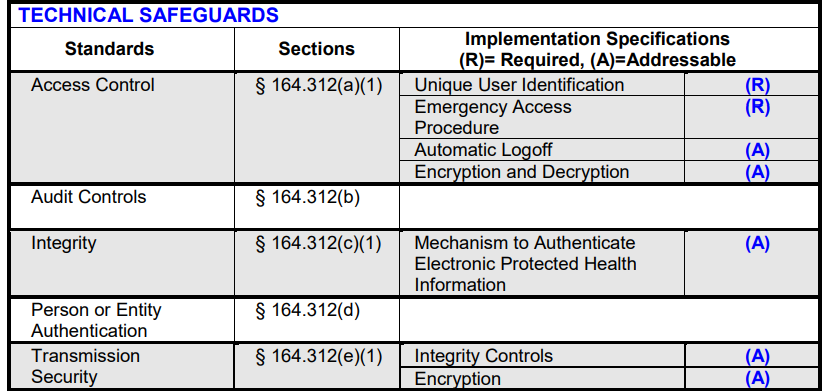
"Required" (R) specifications are mandatory measures. "Addressable" (A) specifications may not be implemented if neither the standard measure nor any reasonable alternatives are deemed appropriate (this decision must be well-documented and justified based on the risk assessment).
Here are the mandatory and addressable requirements for a HIPAA-compliant database.
Mandatory HIPAA Database Security Requirements
HIPAA Compliant Database Access Control
Database authentication. Verify that a person looking for access to ePHI is the one claimed.
Database authorization. Restrict access to PHI according to different roles ensuring that no data or information is made available or disclosed to unauthorized persons.
Encrypted PHI
PHI must be encrypted both when it is being stored and during transit to ensure that a malicious party cannot access information directly.
Unique User IDs
You need to distinguish one individual user from another followed by the ability to trace activities performed by each individual within the ePHI database.
Database security logging and monitoring
All usage queries and access to PHI must be logged and saved in a separate infrastructure to archive for at least six years.
Database backups
Must be created, tested, and securely stored in a separate infrastructure, as well as properly encrypted.
Patching and updating database management software
Regular software upgrades, as soon as they are available, to ensure that it’s running the latest tech.
ePHI disposal capability
Methods of deleting ePHI by trained specialists without the ability to recover it should be implemented.
By following the above requirements you create a HIPAA-compliant database. However, it’s not enough. All HIPAA-compliant databases must be settled in a high-security infrastructure (for example, cloud hosting) that itself should be fully HIPAA-compliant.
HIPAA-Compliant Database Hosting
You need HIPAA-compliant hosting if you want either to store ePHI databases using services of hosting providers, or/and to provide access to such databases from the outside of your organization. Organizations can use cloud services to store or process ePHI, according to U.S. Department of Health & Human Services.
HIPAA compliant or HIPAA compliance supported?
Most of the time, cloud hosting providers are not HIPAA compliant by default but support HIPAA compliance, which means incorporating all the necessary safeguards to ensure HIPAA requirements can be satisfied.
If healthcare business wants to start collaborating with a cloud hosting provider, they have to enter into a contract called a Business Associate Agreement (BAA) to enable a shared security responsibility model, which means that the hosting provider takes some HIPAA responsibility, but not all.
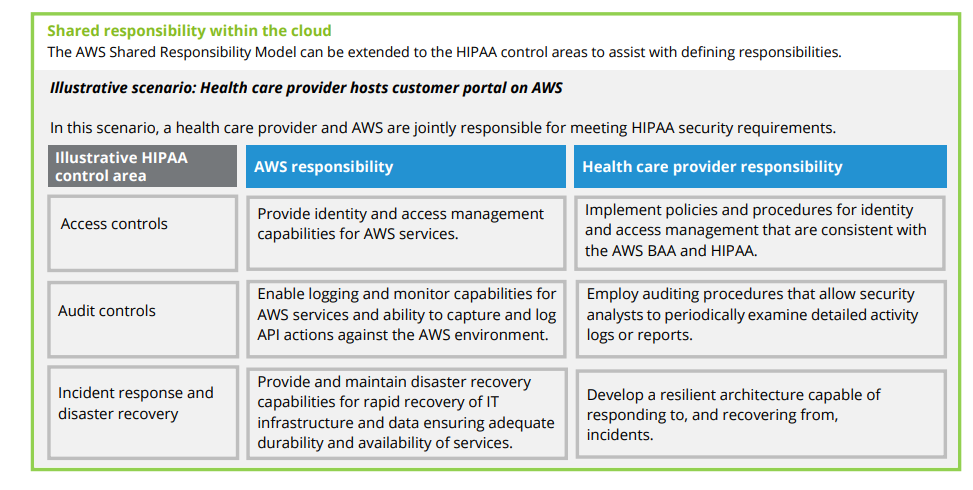
deloitte.com/content/dam/Deloitte/us/Documents/risk/us-hipaa-compliance-in-the-aws-cloud.pdf
In other words, it is possible to utilize HIPAA compliance supported services and not be HIPAA compliant. Vendors provide tools to implement HIPAA requirements, but organizations must ensure that they have properly set up technical controls - it's their responsibility only. Cloud misconfigurations can cause an organization to be non-compliant with HIPAA.
So, healthcare organizations must:
- be ensured that the ePHI is encrypted during transit, in use, and at rest;
- enable data backup and disaster recovery plan to create and maintain retrievable exact copies of ePHI, including secure authorization and authentication even during times where emergency access to ePHI is needed;
- implement authentication and authorization mechanisms to protect ePHI from being altered or destroyed in an unauthorized manner as well as include procedures for creating, changing, and safeguarding passwords;
- implement procedures to monitor log-in attempts and report discrepancies;
- conduct assessments of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI;
- include auditing capabilities for their database applications so that security specialists can analyze activity logs to discover what data was accessed, who had access, from what IP address, etc. In other words, one needs to track, log, and store data in special locations for extended periods of time.
PaaS/DBaaS vs IaaS Database Hosting Solutions
Healthcare organizations may use their own on-premise HIPAA-compliant database management solutions or utilize cloud hosting services (sometimes with managed database services) offered by external hosting providers.
Selecting between different hosting options is often selecting between PaaS/DBaaS and IaaS.
For example, Amazon Web Services (AWS) provides Amazon Relational Database Services (Amazon RDS) that not only gives you access to already cloud-deployed MySQL, MariaDB, PostgreSQL, Oracle, Microsoft SQL Server or Amazon Aurora relational database management software, but also removes almost all administration tasks (so-called PaaS/DBaaS solution). In turn, Amazon's Elastic Compute Cloud (Amazon EC2) services are for those who want to control as much as possible with their database management in the cloud (so-called IaaS solution).
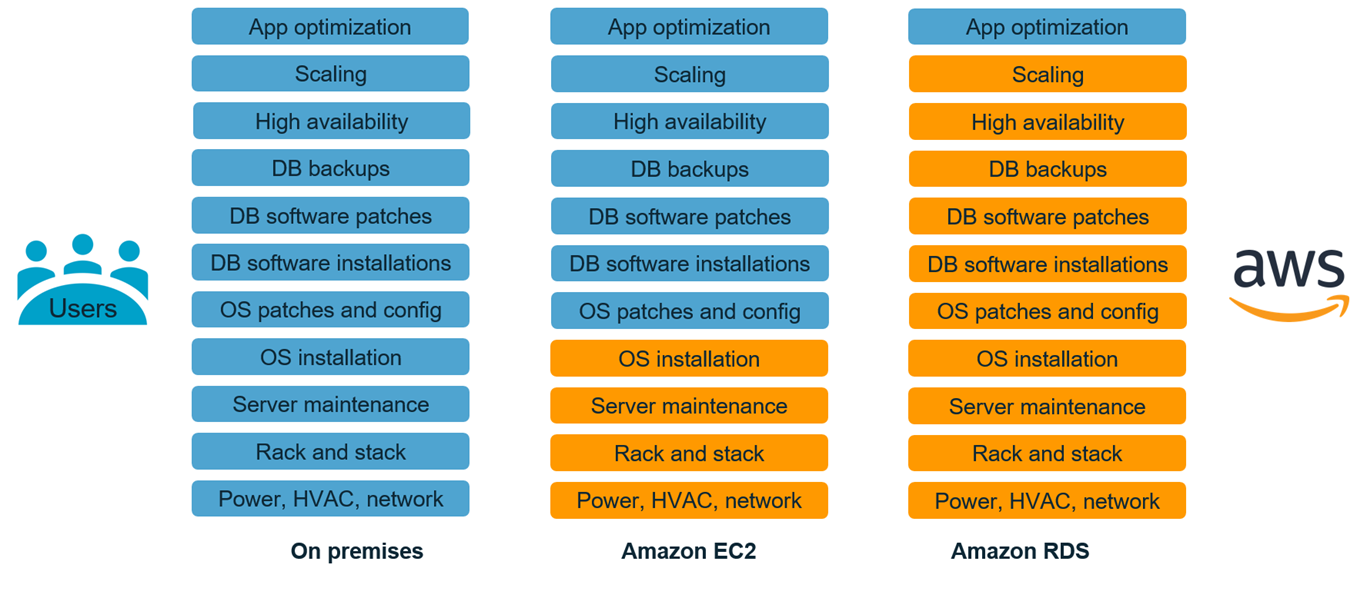
on-Premise vs PaaS/DBaaS vs IaaS Database Hosting Solution
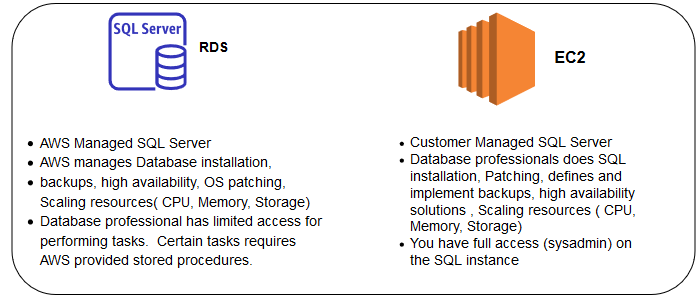
PaaS/DBaaS vs IaaS Database Hosting Solution
Azure also provides relational database services that are the equivalent of Amazon RDS: Azure SQL Database, Azure Database for MySQL, Azure Database for PostgreSQL, and Azure Database for MariaDB. Other database engines such as SQL Server, Oracle, and MySQL can be deployed using Azure VM Instances (Amazon EC2 equivalent in Azure).
Our company is specializing in database development and creates databases for large and smaller amounts of data storage. Belitsoft’s experts will help you prepare a high-level cloud development and cloud migration plan and then perform smooth and professional migration of legacy infrastructure to Microsoft Azure, Amazon Web Services (AWS), and Google Cloud. We also employ experts in delivering easy to manage HIPAA-compliant solutions and technology services for medical businesses of all sizes. Contact us if you would like to get a HIPAA risk assessment and analysis.
Rate this article
Recommended posts
Portfolio
Our Clients' Feedback





















.png)
















Belitsoft has been the driving force behind several of our software development projects within the last few years. This company demonstrates high professionalism in their work approach. They have continuously proved to be ready to go the extra mile. We are very happy with Belitsoft, and in a position to strongly recommend them for software development and support as a most reliable and fully transparent partner focused on long term business relationships.
Global Head of Commercial Development L&D at Technicolor